The Agent is Tripwire’s new generation of agent technology. The Agent is installed on an endpoint to be monitored, and provides data to Tripwire Log Center Manager.
|
Note |
In the past, the Agent has been referred to as the "VIA Agent" or the “Tripwire Common Agent”. These names are still used in the current software, but will be updated in the next release. |
|---|
The Agent can be installed on a wide and growing range of operating systems. For this release, the Agent is supported on:
CentOS Linux 5.3 - 5.11+ (32- and 64-bit)
CentOS Linux 6.0 - 6.5+ (32- and 64-bit)
CentOS Linux 7.0 - 7.1 (64-bit)
Red Hat Enterprise Linux 5.3 - 5.11+ (32- and 64-bit)
Red Hat Enterprise Linux 6.0 - 6.6 (32- and 64-bit)
Red Hat Enterprise Linux 7.0 - 7.1 (64-bit)
Microsoft Windows 7 (32- and 64-bit)
Microsoft Windows 8, 8.1, 8.1 Embedded (32- and 64-bit)
Microsoft Windows 10 (64-bit)
Microsoft Windows Embedded POSReady 7 (32- and 64-bit)
Microsoft Windows Server 2008 SP1, SP2 (32- and 64-bit)
Microsoft Windows Server 2008 R2 (64-bit)
Microsoft Windows Server 2012 (64-bit)
Microsoft Windows Server 2012 R2 (64-bit)
The Bridge is a component through which Agents deliver data to a Tripwire Log Center Manager. To connect with Agents, the Bridge on a Tripwire Log Center Manager uses the Transport Layer Security (TLS) protocol. Therefore, each Agent needs a set of X.509 certificates in order to communicate with the Bridge.
Agents can use two different methods to obtain the certificates used for securing the connection with the Bridge:
with the registration method, you create a pre-shared key that is used to authenticate a newly-connected Agent while it obtains a certificate to use for subsequent connections. To install an Agent using the registration method, see Installing the Agent Using a Pre-Shared Key.
with the public key infrastructure (PKI) method, you create certificates and build a certificate key store on both the Agent and Bridge systems. To install an Agent using PKI, see Installing the Agent Using PKI.
|
Tips |
Tripwire strongly recommends using the registration method unless you have an existing centralized public key infrastructure and are comfortable with creating and maintaining certificate keys. The registration method is equally secure, and greatly simplifies the configuration process. Changing the authentication method after the initial installation will require modifying all existing Agents to configure new certificates. |
|---|
With the registration method, the Agent and Bridge complete the following steps:
| 1. | The Agent establishes an anonymous TLS connection with the Bridge. |
| 2. | The Agent sends an X.509 Certificate Signing Request (CSR) to the Bridge. If the Agent has a registration pre-shared-key file, the pre-shared key is included in the request. |
| 3. | The Bridge verifies the CSR and pre-shared key, and it sends the Agent a set of signed X.509 certificates. |
| 4. | The Agent reads the response and locally stores copies of 1) the Bridge Certificate Authority (CA), and 2) the signed certificates. |
| 5. | The Agent disconnects from the Bridge and deletes its registration_pre_shared_key.txt file. |
| 6. | With the signed certificates, the Agent reconnects with the Bridge and establishes a secure TLS session. |
With the PKI method, the Agent connects with the Bridge using the signed certificates and establishes a secure TLS session.
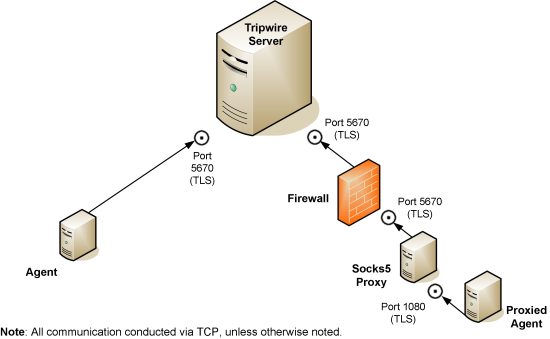
The tables in this section list the services installed with Tripwire Log Center Manager, and the default ports used. Figure 23 illustrates these connections.
|
Service Name |
Listening |
Requires Firewall Access? |
Description |
|---|---|---|---|
|
TripwireBridge |
5670 |
Y |
The Agent's connection port to the Bridge. |
|
Default Port/Protocol |
Configurable During Installation? |
Description |
|---|---|---|
|
5670/TCP/TLS |
No |
Used for inbound communication received from Agents. |
Figure 23. Agent ports and protocols

Before installing the Agent for use with Tripwire Log Center, we recommend that you follow the steps below.
If your TLC environment includes any Windows systems from which the WinLog Collector has previously collected log messages, Tripwire recommends that you migrate those Assets to the Advanced Windows Collector.
To identify Assets that should be migrated to the Advanced Windows Collector, run the Duplicated Assets for Advanced Windows Collectors Report in the Report Center. For instructions, see Running a Report.
To migrate an Asset from the WinLog Collector to the Advanced Window Collector, install the Agent on the Asset's host system, and then assign the Advanced Windows Collector to the Asset in the TLC Console (see Working with Assets).
If your TLC environment included any Windows and/or Linux systems from which the File Collector has collected log messages, Tripwire recommends that you migrate those Assets to the Advanced File Collector.
To identify Assets that should be migrated to the Advanced File Collector, run the File Collector Assets Report in the Report Center. For instructions, see Running a Report.
To migrate an Asset from the File Collector to the Advanced File Collector, install the Agent on the Asset's host system, and then assign 1) the Advanced File Collector and 2) the system's Log Source(s) to the Asset in the TLC Console (see Working with Assets and Working with Log Sources for an Advanced File Collector).